7 Threema Messenger Vulnerabilities Put Millions of Users at Risk

While Threema’s developers promised “special attention to security,” researchers found loopholes in the messenger that allow fraudsters to clone accounts, read correspondence. And to create compromising material for blackmail purposes. It looks like the alternative to Signal and WhatsApp is not so worried about customer privacy.
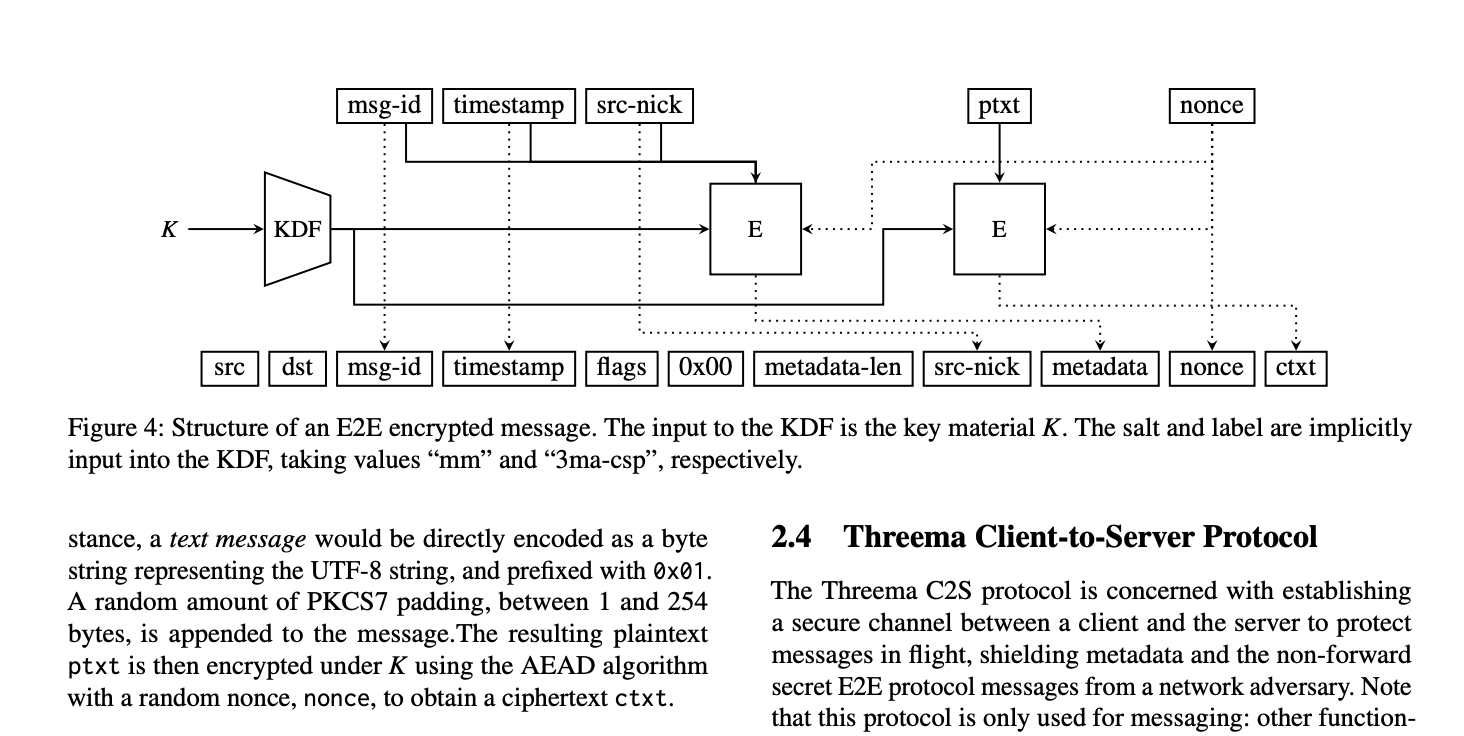
Researchers at ETH Zurich have published a detailed document with the conclusions about the safety of the messenger. Researchers described 7 attacks on Threema protocol. This includes stealing private keys, hacking authentication, and spoofing servers.
The vulnerabilities allow hackers to:
- to access the Threema servers to play back old messages.
- to change the order or delete messages in a dialog.
- to clone an account and send messages on behalf of the victim. For example, compromising material or false confession of a crime.
The creators of the messenger were dismissive of the report. They consider the problems found to be of little significance.
Another drawback of the Threema protocol, of which it has long been known – the lack of future secrecy property. Having decrypted one message, a hacker will also decrypt the next ones. In order to close the vulnerability, the developers announced a new protocol called Ibex. A more secure one, according to the authors. But it has not yet passed security audits. The creators expect you to take their word for it.
Threema is vulnerable in front of spyware. Once Pegasus gets into your phone, encryption no longer matters. Anything you share in a messenger will become available to attackers.

The developer of the application cannot affect the encryption at the OS level. Therefore, it is powerless against serious attacks.
Entrust the exchange of sensitive information to a sanitized phone and MChat native messenger on an independent Mactrix OS with three-layer encryption:
- at the OS level
- at the application level
- at the network stack level
Purchase peace of mind for your secrets in front of hackers and Pegasus. Check out our security consultant’s outline presentation: